YubiKey
You can always carry YubiKey with you as a password. With it, you can lock any device, making it impossible for any hacker to unlock the device without possessing the YubiKey. It is very easy to use, and anyone can use it with ease. Typically, a YubiKey is used to provide strong and reliable security to a device. Below are the details on how to use it. YubiKey is a hardware security key that provides strong two-factor authentication (2FA) and helps protect against phishing and account takeovers.(gadgets commonly used in cybersecurity)

How YubiKey work?
Setting up your YubiKey is similar to setting up a 2FA app. If you’re using a YubiKey (and not another hardware authenticator), follow these steps:
- Insert your YubiKey into a USB port.
- Visit Yubico.com/setup and locate your specific device.
- Under “Compatible accounts and services,” review the supported apps and services, and choose the ones you wish to secure using your YubiKey.
- Your selections will be displayed alongside the available apps.
- Click the play button next to your chosen app to follow the video setup instructions. Alternatively, click the arrow icon within a box to access the text-based setup guide.
Firewall Appliance
Firewall Appliance is a device that basically checks the traffic of the incoming network and outgoing network between a device. Before using Firewall Appliance, some rules and regulations are given in advance in the device on which it will be used. Basically, this Firewall Appliance works and if any network wants to enter outside the rules regulation, this Firewall Appliance blocks that network, and thus
Basically Firewall Appliance works.
Basically it’s a Hardware devices like Cisco ASA, Palo Alto Networks firewall, or similar, which provide network security by filtering incoming and outgoing traffic based on predefined security rules.
There are multiple types of firewalls based on their traffic filtering methods, structure, and functionality.
1.Packet Filtering
2.Stateful Inspection
3.Proxy Service Firewall
4.Next-Generation Firewall
5.Unified Threat Management (UTM) Firewall
6.Threat-Focused NGFW
New facilities to rescue hacked YouTube channels
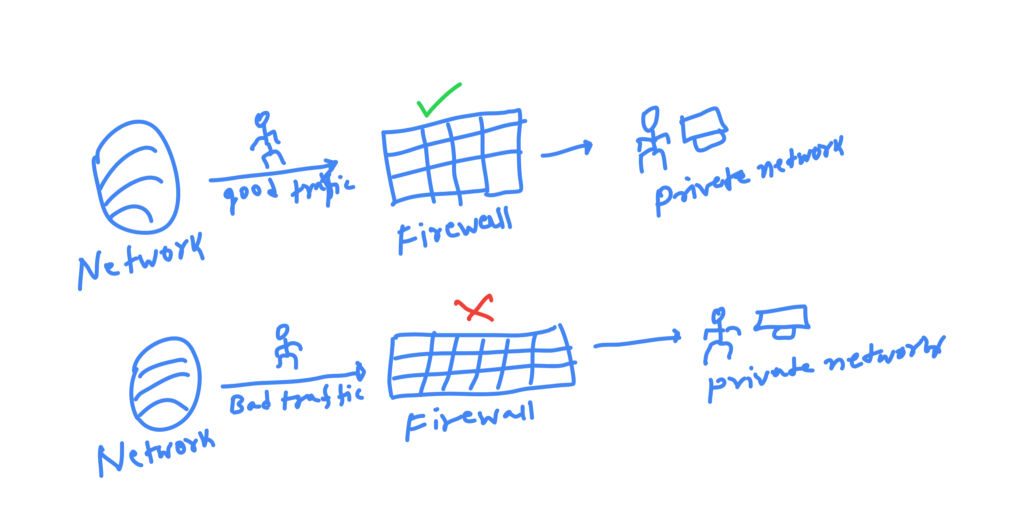
How Firewall Work?
Firewall basically works on what instructions are set in it, if Firewall gets
a good network it will allow it to access the network’s website and if it gets a bad network it will not allow it to access the website.
USB Data Blocker
USB Data Blocker
A device that you will mainly use during the charger of your device, when you use a public charger cable, you have to connect the USB Data Blocker to that charger and charge it, as a result, any Unauthorize your phone or other devices through that cable. can’t enter
ans also it is a A small device that prevents accidental data exchange when charging your devices via USB ports, protecting against data theft or malware injection.
How Does A USB Data Blocker Work?
USB data blockers, despite their small size and low cost, are crucial for maintaining control over how you charge your device securely. Here’s how to use them effectively:
1.Insert the data blocker into the public USB port.
2.Connect your charger cable directly to the data blocker.
3.Plug the assembled connection into your phone as usual.
4.By following these steps, your phone can charge without risking any unintended data transfers with potentially harmful third parties.
RFID Blocking Wallet
The full meaning of RFID is “Radio Frequency Identification”
An RFID-blocking wallet or cardholder employs technology that prevents unauthorized access to RFID-enabled credit cards and IDs, thereby protecting against electronic pickpocketing.
RFID blocking involves protecting your RFID-enabled devices from unauthorized access. One common method to achieve this is through an RFID blocking wallet, which shields your cards using materials designed to disrupt electromagnetic fields.

How Does RFID Blocking Wallet Work?
1.A reader sends out specific radio frequencies to initiate a signal that activates the electronic tag on the object.
2.Once activated, the tag uses energy from the electromagnetic waves generated by the reader to transmit information back to the reader’s antenna.
3.The reader then electronically translates this transmission into usable data.
Hardware Security Module (HSM)
A hardware security module (HSM) is a physical device designed to securely store cryptographic keys, keeping them confidential and accessible only to authorized users. The main goal of HSM security is to regulate access to an organization’s digital security keys, ensuring that they remain protected from unauthorized access or use.
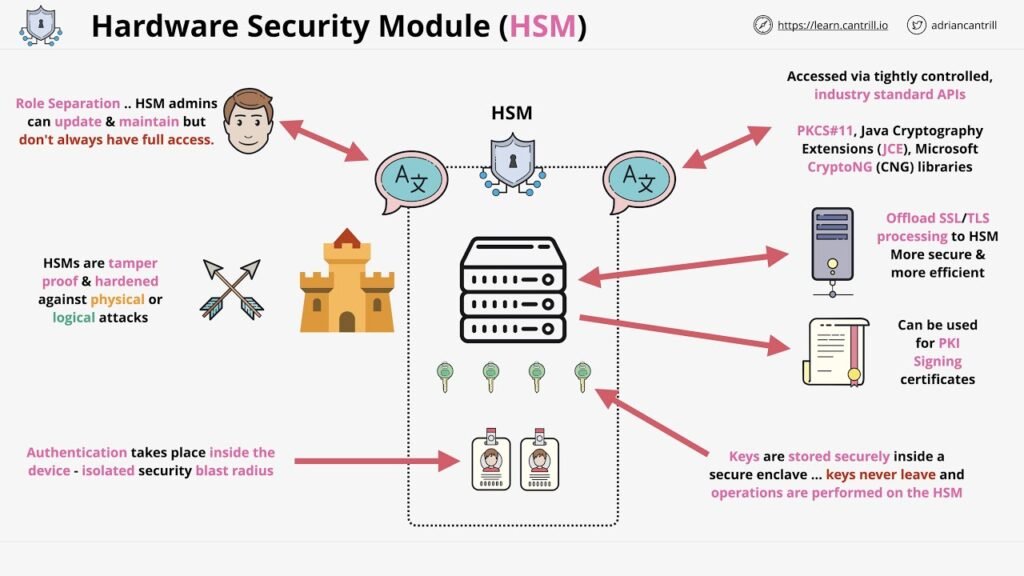
How Hardware Security Modules (HSMs) Work?
Hardware security modules (HSMs) prevent an application from loading a copy of a private key into the memory of a web server. This is crucial because security keys stored on web servers are vulnerable to exploitation by hackers. If attackers gain access to the server, they can locate these keys and potentially access sensitive data.
By implementing either an in-house HSM system or utilizing a HSM-as-a-Service model, organizations can significantly mitigate the risk of unauthorized access to their data. This approach helps safeguard against potential breaches and reinforces data security measures effectively.
